enterprise app development firm | web and mobile app development agency | custom software development company | Software Agency in Ethiopia | Software Development Ethiopia | Software Team | Website Development | App Development | Agency | Software Solutions | Web app Developer | App developer | Website Developer | IT Solutions | Software Company Ethiopia | Software Development Company Ethiopia | Software Development Firm Ethiopia | Software Development Services Ethiopia | Custom Software Development Ethiopia | Software Consulting Ethiopia | IT Consulting Ethiopia | Digital Transformation Ethiopia | Technology Solutions Ethiopia | Software Engineering Ethiopia | Agile Software Development Ethiopia | Full-Stack Development Ethiopia | Mobile App Development Ethiopia | Web Development Ethiopia | Enterprise Software Ethiopia | Cloud Solutions Ethiopia | SaaS Development Ethiopia | E-commerce Solutions Ethiopia | UI/UX Design Ethiopia | Software Maintenance Ethiopia | Software Support Ethiopia | IT Services Ethiopia
About Us
Our Mission
We are driven by a single purpose: to build Solution that accelerates your business, not complicates it. We focus on lean, scalable, and secure architecture, translating complex business challenges into elegant digital solutions that deliver measurable ROI.
The Core Team & Expertise
Our team is a carefully curated blend of senior architects, seasoned developers, and dedicated Graphics and UX/UI designers. We specialize in modern frameworks and cloud infrastructure, ensuring your project is handled by specialists who live and breathe high-performance technology.
Our Development Philosophy: Uptime & Scale
We operate on principles of transparency, iteration, and absolute reliability. We prioritize comprehensive testing and DevOps automation to ensure the 'Maximum Uptime' we promise is delivered. We don't just build code; we build dependable systems ready for global scale.
Why Choose Our Custom Approach?
Off-the-shelf solutions often fail to meet unique business demands. Our 'Offers Choice' promise means we tailor every feature and integration to fit your exact processes, eliminating bottlenecks, providing unparalleled flexibility, and safeguarding your long-term success.
How we implement Your our Projects
We implement your projects through a structured timeline that ensures transparency and efficiency at every stage. From initial consultation to final delivery, we keep you informed and involved, guaranteeing that the end result aligns perfectly with your vision.
Concept
Concept
During this initial phase, we conduct thorough Discovery and Research to lay a precise foundation for the entire project.
UI/UX Design
UI/UX Design
We begin with Wireframing and Prototyping to visualize the complete user experience.
Development
Development
We translate approved designs into production-ready software using agile sprints.
Testing & QA
Testing & QA
Rigorous testing ensures stability, performance, and security.
Deployment & Go Live
Deployment & Go Live
We deploy and configure production infrastructure for seamless launch.
Maintenance & Support
Maintenance & Support
Continuous monitoring and proactive maintenance keep systems reliable.
Our Services
Mobile
Development
We engineer high-performance iOS and Android applications tailored to specific business needs, ensuring a seamless user experience through modern features and robust security protocols.
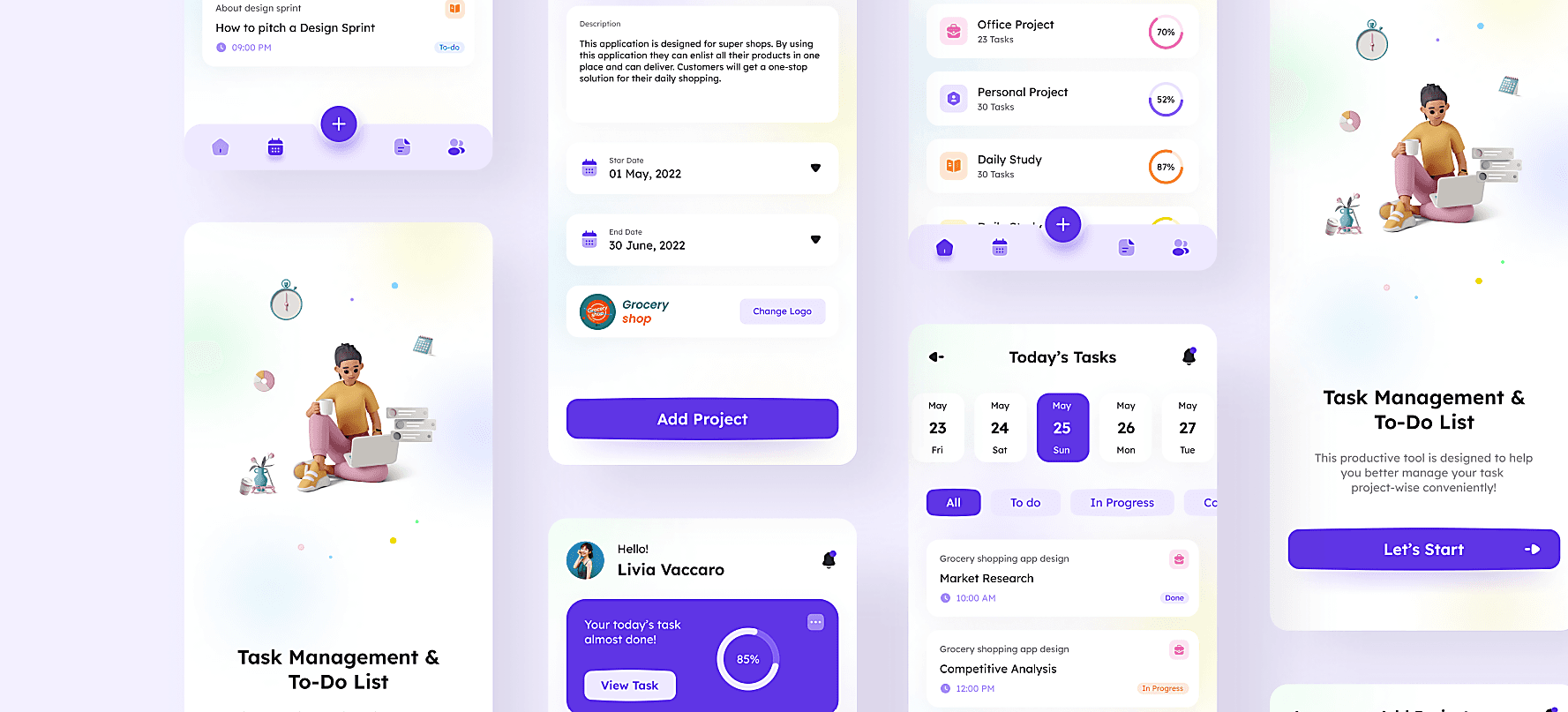
Website
Development
Our team architected fast, responsive, and SEO-optimized web applications that scale with your growth, utilizing the latest technologies to deliver a powerful digital presence for your brand.
UI / UX
Design
We focus on user-centric design principles to create intuitive interfaces and engaging experiences, blending aesthetic beauty with functional simplicity to maximize user retention.
Graphics
Solutions
Elevate your brand with professional visual identity services, including custom logos and high-impact marketing materials that effectively communicate your company's core values.

System
Maintenance
We provide comprehensive system audits, regular software updates, and proactive security maintenance to ensure your digital infrastructure stays secure, efficient, and downtime-free.

Portfolios
Why Agelgl is the Right choice for you?
Product Partnership, Not Outsourcing
We embed into your business model and decision process, ensuring the software supports how you actually operate, not how a template assumes you should.
Engineered for Long Term ROI
Every system is architected for maintainability and controlled growth, reducing rework, technical debt, and unnecessary future spending.
2 Months Free Post Launch Maintenance
After delivery, we provide two months of free maintenance to stabilize your system, fix edge cases, and ensure smooth real world operation before any support contract begins.
Radical Transparency Process
You receive full visibility into progress, decisions, and tradeoffs through structured milestones, demos, and clear technical documentation.
What makes our infrastructure secure?
We implement multi-layered defense strategies to ensure your data, infrastructure, and users remain protected at every stage.
Security by Design Architecture
Every system begins with threat modeling, trust boundary definition, and least privilege rules enforced at the architecture level.
Strict Access Control and Secrets Management
All credentials are stored in secure environment vaults with role based access control across application, database, and infrastructure layers.
Hardened API and Authentication Flow
APIs use token based authentication, refresh rotation, rate limiting, and anomaly detection to block abuse and intrusion attempts.
Data Protection at Rest and in Transit
All connections are encrypted and sensitive records are protected at the database layer with controlled key rotation.
Automated Dependency and Vulnerability Scanning
Every deployment is scanned for outdated packages, license risks, and known vulnerabilities before release approval.
Isolated Environments and Deployment Controls
Development, staging, and production are fully isolated with zero direct production access and automated rollback mechanisms.
Logging, Monitoring, and Incident Readiness
Real time alerts, audit trails, and structured logging detect suspicious activity early and support rapid incident response.
Client Ownership and Handover Security
Full security documentation, access control guides, and secret rotation playbooks are delivered at project handover.
Ready to bring solution
for your Business?
Phone
+251986190354
+251954704213
contact@agelgl.com
Address
Bole, Addis Ababa, Ethiopia